On 11th March 2020, HPE announced its latest Small Business Solutions, leading with its next-generation HPE ProLiant MicroServer Gen10 Plus featuring remote management and security capabilities, with a choice of Intel® Pentium or Intel Xeon E processors. Solutions tailored for small businesses includes Office in a Box, Scalable File and Backup as well as Edge to Cloud for simplified access to cloud services.
Tough economic times bring investment decisions into sharp focus. The result is typically lower investment levels. It also sharpens medium- and longer-term priorities. That leads to smart investments. But also, investments made at this time become longer term drivers of investment for adjacent areas. Techaisle believes that the recent economic implosion acts as a catalyst for such action and change among SMBs. In a digital economy, SMBs are able to expand reach and engagement with customers and prospects, while also locating and integrating with suppliers to improve scale-out options. 79% of SMBs are on the road to digital transformation. The roadmap to successful digital transformation begins with the creation of a sound physical infrastructure - the ‘building blocks’ or ‘foundations’ of business infrastructure. Core infrastructure devices need to be kept in sync with the requirements of digital transformation initiatives; servers, storage, networking and security need to advance with the needs of the organization. The most advanced and transformative SMB firms are looking to improve IT sustainability – their ability to effectively manage IT delivery into the future – customer intimacy, operational excellence and IT’s speed and agility. And they are seeing better business outcomes than those which are not fully committed to the core physical infrastructure modernization.
HPE solutions lay the foundation for effective, agile and secure modernization.
First Impression
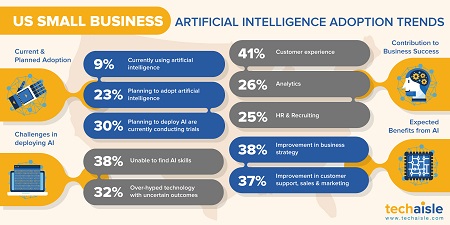
HPE ProLiant MicroServer Gen 10 Plus and companion offerings should be no-brainer for small businesses and channel partners. Techaisle data shows that 83% of SMBs consider technology contributing to business success but they also find technology to be kinetic, complex and risky. Regardless, 31% of small businesses want to modernize IT infrastructure and HPE offerings help in overcoming cost of implementation (34%) and security concern (32%) inhibitors of embarking on IT modernization initiative. Techaisle data also shows that a growing percent pf SMBs are using both on-prem and cloud servers, but hybrid is where they are headed. Workloads from public clouds are transitioning to hybrid clouds with 70% of small businesses are either implementing or planning to use basic hybrid cloud with workloads assigned to different cloud/on-prem environments. Techaisle segmentation data reveals that there is a higher demand for on-prem solutions within SMBs that are intermediate and mature cloud adopters as well as those who are in the basic and advanced IT maturity segments. HPE ProLiant MicroServer Gen10 Plus and Office in a box can also be easily adopted and deployed by the Pre-IT maturity segments and passive cloud followers.
HPE ProLiant MicroServer Gen10 Plus
About the size of a typical hardcover book (4.6-inch x 9.65-inch x 9.65-inch) and as quiet as a library (36db) the server packs enough power and storage for a small business prompting HPE to call it “small and Mighty”. The form factor size is volumetrically 3X less than that of Dell PowerEdge R240. As-a-service server pricing starts from at less than US$20 per month. The list price varies from US$$709 to US$899, for Entry to Performance level configurations.
Three key features of HPE ProLiant MicroServer Gen 10 Plus worth calling out are:
- HPE-exclusive silicon root of trust that provides 360-degree protection, detection and recovery from malicious cyberattacks. Techaisle SMB security adoption survey data shows that for 53% of SMBs cyberattack security is either the most critical or among the top three critical issues facing their organizations but 78% are not confident that they can recover from a cybersecurity incident. With HPE silicon root of trust they may have one less issue to worry about.
- HPE ILO 5 that delivers server health and operations insights with secure remote monitoring and management. With an average of 3.8 IT staff within upper-small businesses, SMBs need help in remote monitoring of IT infrastructure. Manageability is an important solution selection criterion for SMBs which typically have relatively small IT workforce but expansive IT/digital transformation goals. In this environment, it is essential that solutions work seamlessly and without a great deal of hands-on management.
- HPE InfoSight for Server that predicts and prevents IT disruptions before business operations are impacted. In the context of growth, cloud is seen as a means of facilitating expanded reach. And SMB cloud adopters are looking for capabilities that contribute to growth: 79% report that cloud enables them to be more agile in their business operations. Cloud built on a strong core technology is not only an essential IT infrastructure but it is also an imperative business infrastructure.
Pre-configured small business solutions on HPE ProLiant MicroServer Gen10 Plus
Office in a box: is a pre-configured solution that includes HPE ProLiant MicroSever Gen10 Plus with built-in security, Aruba Instant On (wireless access point), and HPE RDX removable disk system which can be scaled when required. It is ideal for very small businesses, small offices, small workgroups for up to 10 users. Office in a box also comes with Windows ROK (Reseller Option Kit) and storage controller. Pricing starts at US$125 per month. As per Techaisle’s SMB buyers’ journey and technology research data, nearly 2/3rd of small businesses use existing IT budgets and about 1/5th use CAPEX dollars for IT purchases. For these small businesses, HPE has a list prices for Office in a box. For example, a configuration consisting of MicroServer Gen10+, 4 1TB drives, iLO enablement, Next Business Day support, one Aruba WAP (wireless access point), the list price is approximately US$3,500 before discounts. Only 3% of small businesses have full-time IT staff (Source: Techaisle SMB and Midmarket research) and very small businesses manage workloads with a much smaller staff, typically comprised of IT generalists, and have limited infrastructure resources available for exploration. There is a very short line between acquisition and deployment of new technology and they have fewer chips to place on the table, and need to quickly reap return from their investments. Office in a Box is suitable for both segments of small business – with internally-managed-IT and un-managed-IT.
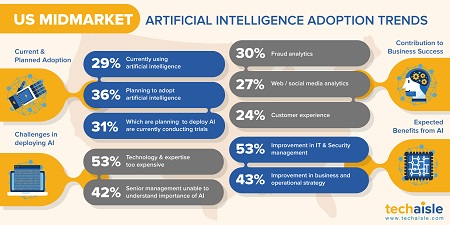
Scalable file and backup: is a pre-configured solution for centralized access to files for easy and secure collaboration. Scalable up to 16TB the solution enables secure onsite backup and recovery. Businesses are heavily invested in IT, with IT-dependent processes throughout their operations. This ubiquitous dependence on technology means that any systems failure will reverberate throughout all of a company’s daily operations. There is no way to disaster-proof against IT failure with insurance. Appropriate investment in IT backup/DRS, security processes, technologies and management strategies are the only ways to capitalize on the productivity benefits of IT without creating exposure to organizational paralysis in the event of a malware invasion, a hacker attack or an employee’s negligence or malfeasance. Techaisle’s SMB and midmarket security adoption trends research shows that 53% of small business and 48% of midmarket firms prefer less than 1 hour of backup recovery time. Not all SMBs have a backup/DRS strategy because they find it either too expensive or worry about security in the cloud or even find a solution too complex. HPE’s pre-configured solution addresses the needs and objections.
Edge to Cloud: is a pre-configured solution for remote office, branch office (ROBO) deployments. The solution includes optional cloud services for connectivity to the core data center.
Techaisle Take
Techaisle believes that the 34% of SMBs that are prioritizing growth are much more likely to thrive in today’s unpredictable economy than those that focus primarily on cost reduction or other ‘business as usual’ objectives. In the digital world, growth is more than simply increasing the top line. Today, growth is important to both expansion and to maintaining viability. Techaisle’s SMB research has found that the need to be more efficient in operations is the single most compelling reason for SMBs to embrace digital transformation. But there have to be points in the system where the capabilities of core infrastructure connect to the promised benefits of digital transformation solutions. The days of using lengthy, detailed cost analyses to justify new IT systems are disappearing in favor of a more agile approach in which businesses are encouraged to try new approaches and to rapidly wind down these initiatives if they do not deliver anticipated benefits. This may sound like a recipe for an out-of-control spending, but there are options that can protect the cost line. HPE ProLiant MicroServer Gen 10 Plus is one such options which is mind-blowing and should be a no-brainer.