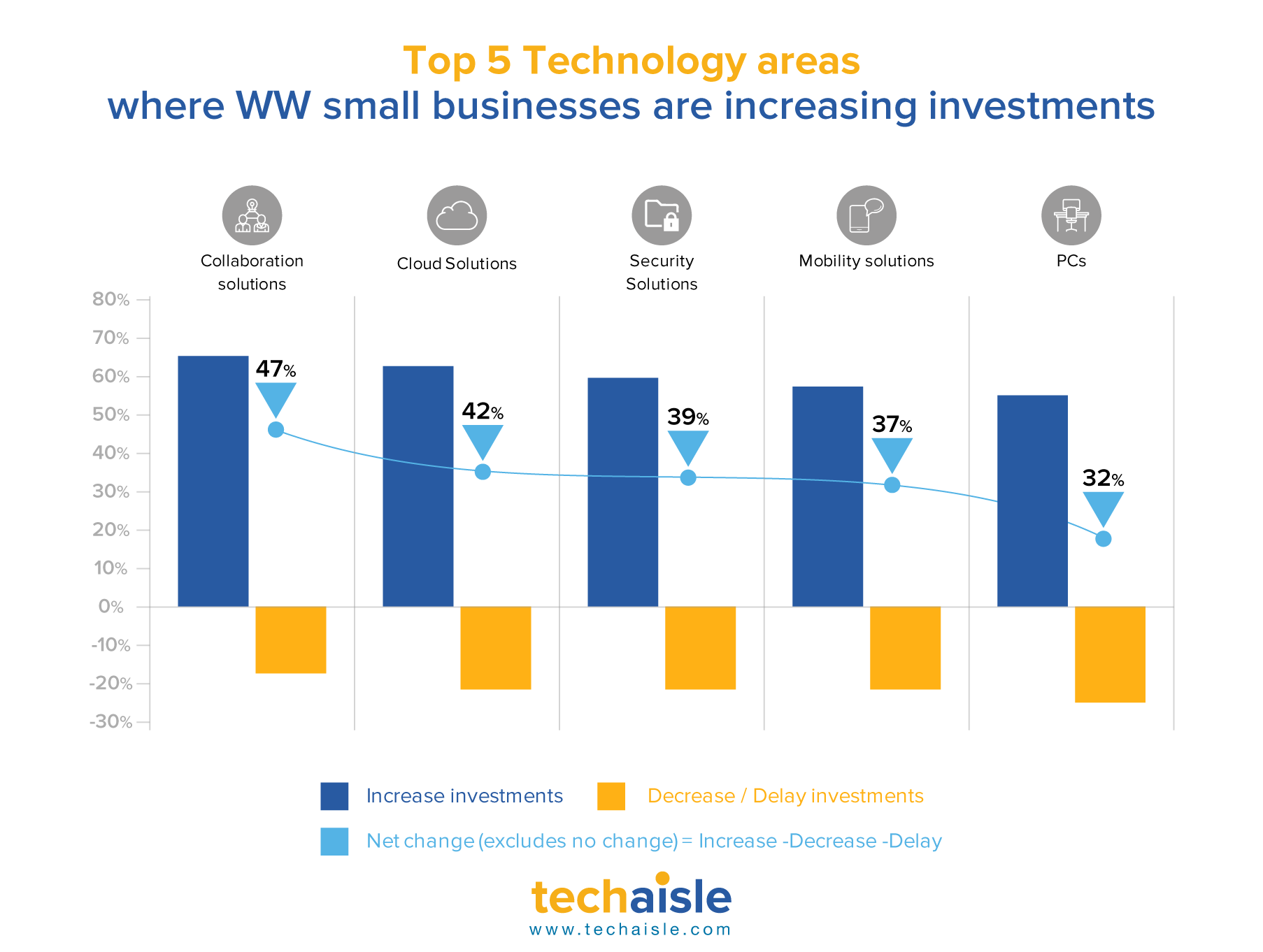
Techaisle worldwide survey of midmarket firms shows that collaboration, security, cloud, remote work and digital transformation are the top five areas where midmarket firms are increasing technology investments.
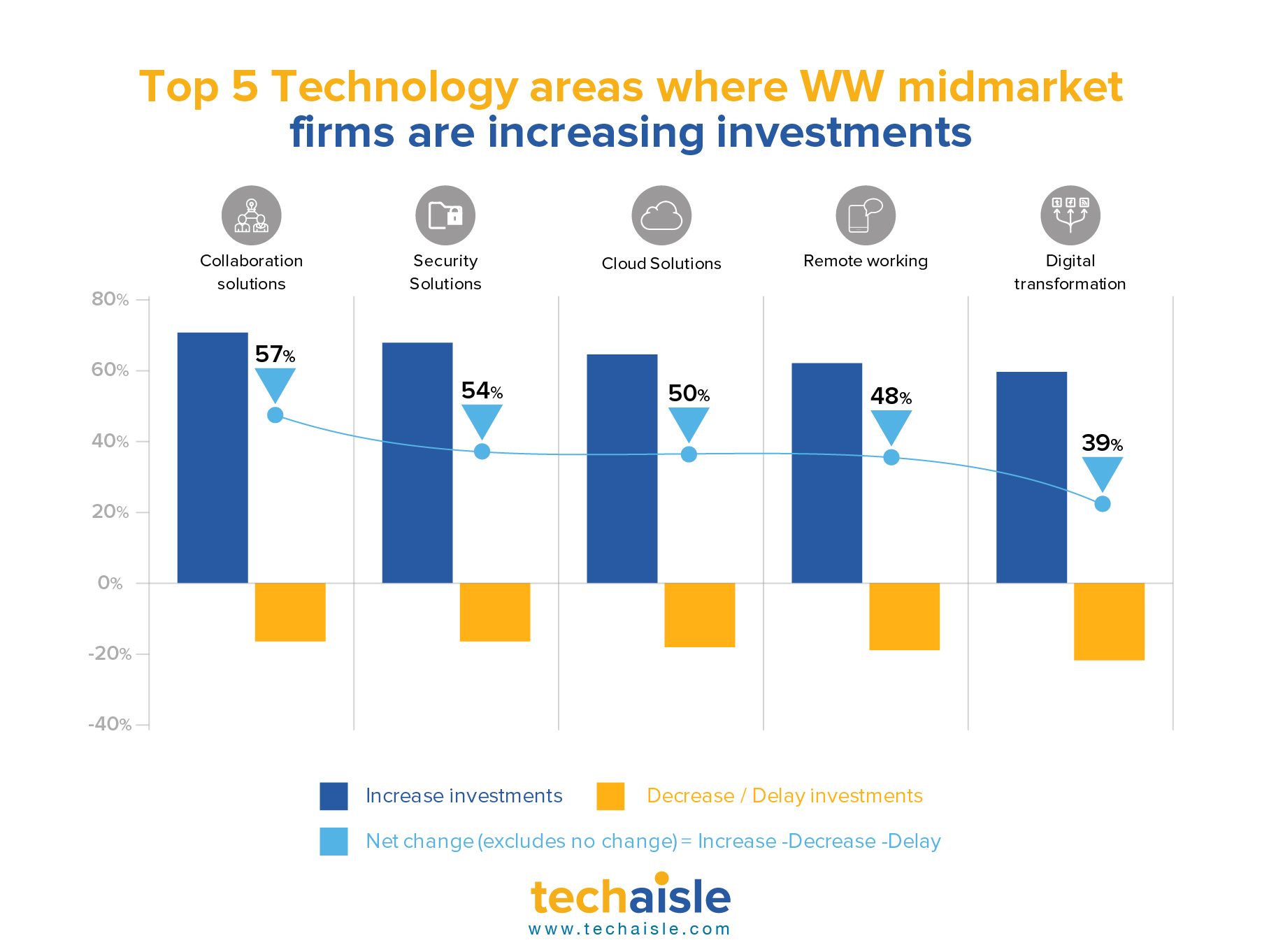
Collaboration: 72% of midmarket firms are increasing investments in collaboration solution as compared to 15% who are either decreasing or delaying investments. Collaboration is a central component to virtually all business activities and is evolving in response to new market conditions and those collaborative technology solutions are being acquired which are positioned as a framework that integrate and extend the value of discrete capabilities, rather than as a “first step” platform.
Security: 69% of midmarket firms are increasing investments in security solutions. IT security is no longer being viewed as a necessary and unwelcome cost, rather as an enabler of business solutions, a viewpoint that is reinforced by a clear need for IT security in the face of increasing threats to information security and business continuity. Effective security practices are going beyond merely “raising the shields” around users, data and networks – they are being seen as enabling innovation throughout the IT/business infrastructure.
Cloud: 66% of midmarket firms are increasing investments in cloud. Cloud addresses real-world IT issues and business challenges. Cloud represents a powerful way of addressing budget constraints: cloud infrastructure can be deployed quickly and at low cost. Cloud is linked with mobility solutions, particularly security solutions, as data that is accessed via a mobile device can be available anywhere/anytime via cloud, but remain separate from the devices themselves, protecting corporate information from loss or theft or malware. And cloud’s pay-as-you-go approach meshes very well with the need to align IT investment with business benefits.
Remote work: 65% of midmarket firms are increasing investments in remote working. Mobile devices, technologies and services are perhaps the most exciting space today, remaining resilient even in a downturn. Midmarket firms are investing to automate control of sprawling mobile assets. The list includes security solutions (MDM, mobile app security, secure mobile data sharing) that address widespread concern over the exposure that accompanies mobility, as well as methods of automating management (mobile network control, enterprise mobile management) and of deploying infrastructure tuned to the needs of mobile workers (Windows-as-a-Service, VDI, DaaS).
Digital transformation: 61% of midmarket firms are increasing investments in digital transformation. Mature cloud adoption does not equate to high digitization of the business. Data shows that only half of the 47% of mature midmarket cloud adopters are holistic adopters of digitalization. It is true that these firms believe in cloud and its effect on digitization but they also believe that true digital transformation requires advanced adoption of multiple technology solutions. The roadmap to successful digital transformation begins with the creation of a sound physical infrastructure - the ‘building blocks’ or ‘foundations’ of business infrastructure.