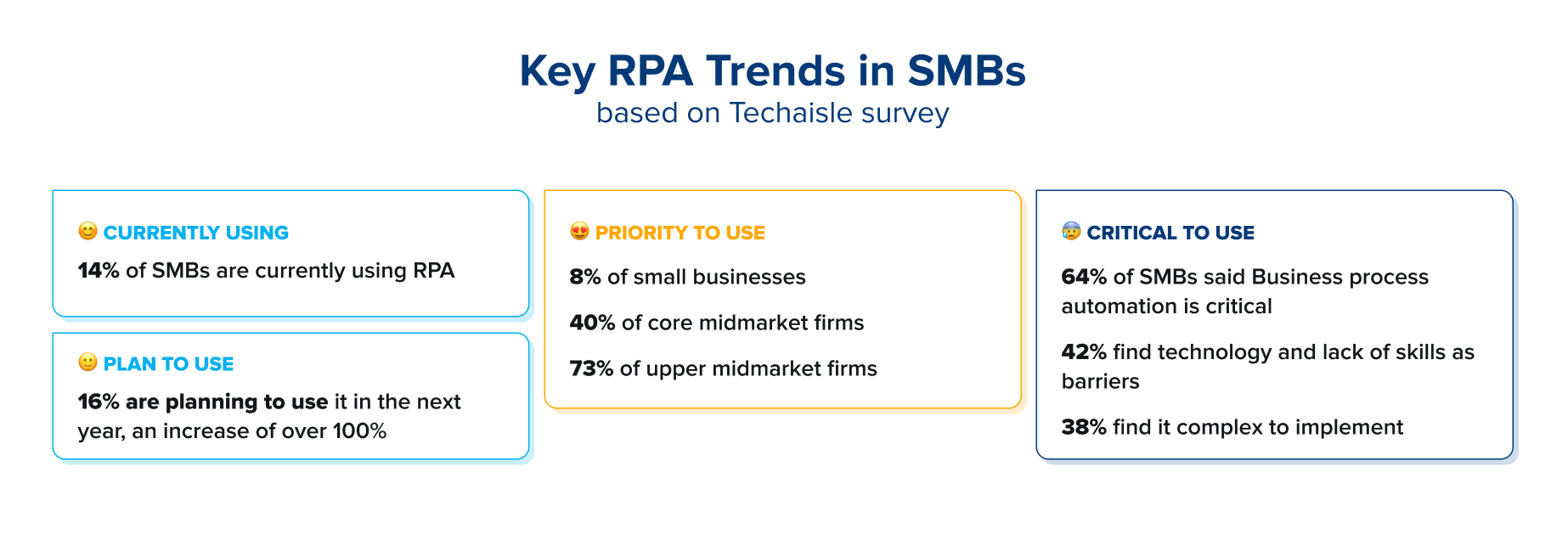
Current trends show that Robotic Process Automation (RPA) adoption rates have risen significantly, with many businesses wanting to automate processes to increase efficiency. RPA is a non-invasive technology for making daily operations more efficient, allowing for increased productivity. While larger organizations have started early, smaller businesses have also begun to adopt RPA increasingly. While there is still some misconception that RPA is not so relevant for SMBs. The rise in adoption can be attributed to the fact that RPA technology helps boost productivity, enhance customer and employee satisfaction, improve cash flow, support audit and compliance requirements, and gain a competitive advantage. SMBs rely on efficient workflows and effective systems throughout all processes, and in the SMB space, efficiency is often a critical competitive advantage.
Importance of RPA to SMBs and midmarket firms
SMBs have constraints, such as limited resources and budgets, that demand flexibility. However, because SMBs are agile, they can quickly adopt new technologies with less friction. Large enterprises are generally burdened with complexity and red tape, but SMBs can embrace change and gain immensely by implementing RPA.
1. Technological competitive advantage: SMBs can improve productivity to gain a competitive advantage by automating repetitive and time-consuming tasks traditionally associated with back-end office functions.
2. Real-time tracking: RPA systems can track, analyze, and estimate an organization’s data in real time. Based on the estimates, SMBs can focus on improving their shortcomings and building their strengths. In addition, the data can be accessed anytime when required.
3. Cost reduction: SMBs often have limited resources and are highly cautious about direct and indirect costs. Hiring more personnel increases business costs, but by adopting RPA, SMBs can handle daily operations with lesser dependency on the human workforce.
RPA Use Cases for SMBs
As RPA technology continues to evolve, its applicability across industries, functions, and systems also expands. Here are some of its SMB use cases.