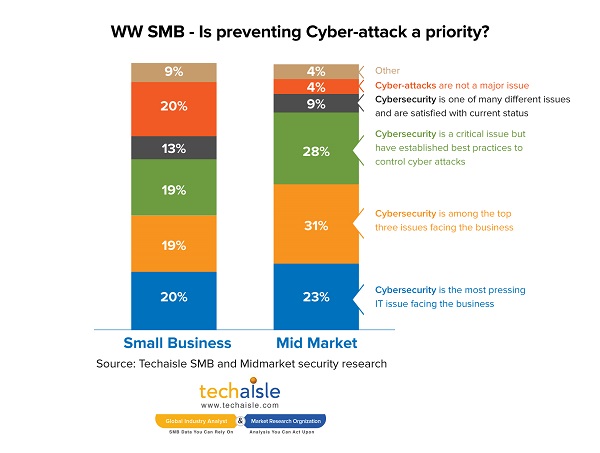
Techaisle’s SMB and Midmarket security solutions adoption research shows that although security is a top IT priority for 85% of SMBs, cybersecurity is still not the most pressing security issue for 80% of SMBs. These SMB firms maybe maneuvering around the edges of cybersecurity flame as 19% of small businesses and 28% of midmarket firms believe that they have established best practices to control cyber-attacks. 31% of SMBs report that they are very confident of recovering from a cybersecurity incident and another 20% say the recovery is dependent upon the type of incidence. Is it really the case that the security-confident SMBs have taken all necessary steps to safeguard data, user and environment? Answer lies in the next set of data points. Only 8% of small businesses and 24% of midmarket firms have tested their responses to breaches or security incidents to ensure that their protocols will be effective in a crisis situation. Less than 10% of SMBs are covered by cyber-insurance and only 5% are considering cyber-insurance.
SMBs that build effective, responsive security frameworks will be positioned to capitalize on new technologies and on the new efficiencies that they enable. There is no denying that the threats that IT security frameworks address are becoming both more pernicious and a greater threat to the success of IT-dependent businesses – which is to say, nearly all businesses.
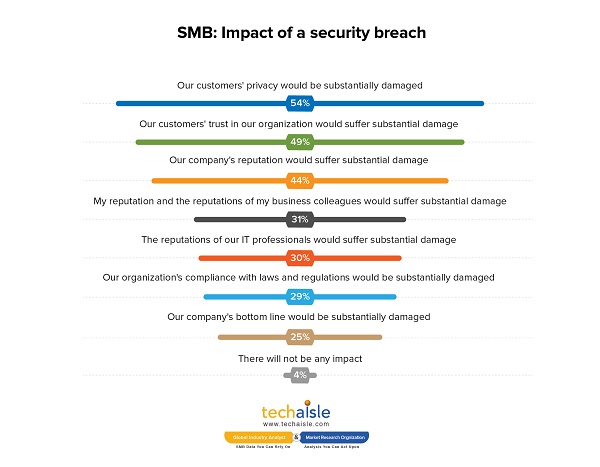
In the Techaisle survey, respondents were asked “– what would be the impact on your organization if there was a security/data breach of corporate information?” Responses indicate that the damage would be widespread and substantial. As the chart below demonstrates, the most severe consequence of a breach would be damage to customer privacy and trust, but there would also be damage to corporate reputations and profitability, difficulty in meeting regulatory requirements, and personal reputation damage for both business and IT professionals within the firm.
The NIST framework does a good job of describing a business’s approach to cyber security, but it doesn’t actually address the approaches used by ‘bad actors’ to attack data and users. To understand how attackers work (and might be stopped), IT security professionals often turn to the cyber (or intrusion) kill chain. This seven-stage view of an attacker’s process, developed by Lockheed Martin in 2011, helps technical leads to align security technology and processes against an attacker’s progressive objectives.
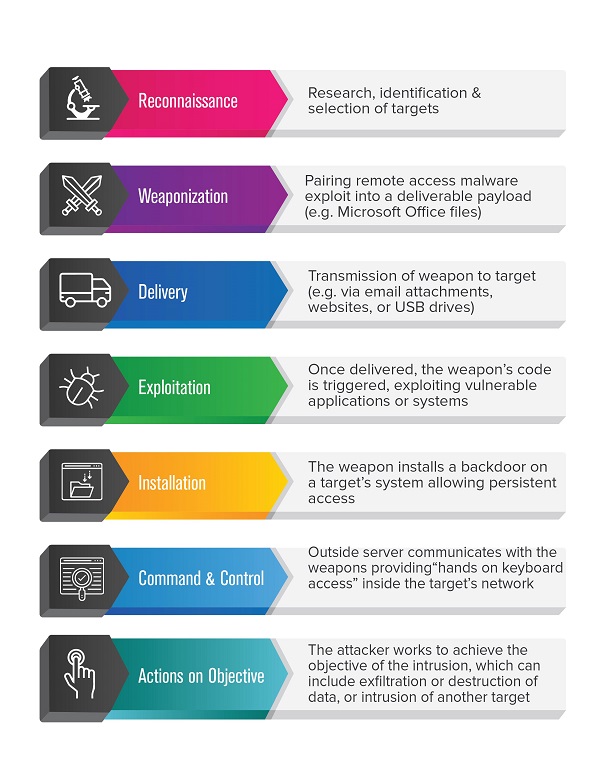
There are many variants on the diagram. Some include responses to the intrusion kill chain, urging businesses to “detect, deny, disrupt, degrade, deceive and destroy” attackers and their malware. Others highlight the key technologies and technology processes used to support these responses: for example, security professionals combating intruders at the reconnaissance stage might use web analytics to detect an intruder’s activities, and then firewall technology to deny access to corporate systems. The specific details vary from scenario to scenario, and evolve over time. What is constant, though, is the need for technically-adept security professionals to invest in capable technologies, to integrate these systems with each other, to develop processes that connect effectively with threats and technology-based ‘shields’, and to align these systems and processes with management’s corporate objectives.
It isn’t an exaggeration to state that in today’s business world, IT infrastructure is business critical infrastructure. SMBs are heavily invested in IT, with IT-dependent processes throughout their operations. This ubiquitous dependence on technology means that systems failure will reverberate throughout all of a company’s daily operations. There is no way to disaster-proof against IT failure with insurance; appropriate investment in IT security processes, technologies and management strategies is the only way to capitalize on the productivity benefits of IT without creating exposure to organizational paralysis in the event of a malware invasion, a hacker attack or an employee’s negligence or malfeasance.
The lack of understanding of a threat associated with a widely-used cloud platform on one hand (and likely, additional confusion with respect to security issues associated with other technologies), and the lack of IT staff resources available to address security concerns on the other, produces a clear conclusion: SMBs need suppliers to step up to delivery of secure IT environments and prevent cyber-attacks.
In many cases, these suppliers will be the mainstream channel partners who supply the SMB’s technology, who act as the IT management presence within the SMB’s business. In other cases, including in many midmarket environments, the source of security products and services will be specialized managed security providers who focus tightly on operating SOCs and protecting client environments. In some scenarios, firms will ‘land’ by entering a client account from one of these positions, and then ‘expand’ to serve a wider range of IT supply needs – crowding out competitors who can’t address the risk and compliance issues that are central to the CEO’s mandate.
Related research
US SMB and Midmarket Security adoption trends
Europe SMB and Midmarket Security adoption trends
Asia/Pacific SMB and Midmarket Security adoption trends
Latin America SMB and Midmarket Security adoption trends












