Techaisle Blog
Xerox: A Different Approach to SMB Security in a Changing World
Security matters to SMBs and midmarket firms - a LOT. Technology is essential to productivity, growth, and profitability – but it exposes SMBs to potentially devastating security breaches. But cybersecurity is a daunting challenge. Technology is so complex, and the threat sources are so menacing that many SMBs practice “security through obscurity:” They hope that attacks will be pointed at larger targets and that they can find safety by keeping a low profile.
The world of cybersecurity is a constantly evolving battleground. Gone are the days of lone hackers targeting specific networks. Today, criminal organizations cast wide nets, hoping to exploit vulnerabilities in increasingly connected devices, from printers to smart TVs. Unfortunately, there are enough hackers, scammers, and cybercriminals to go around – and every conscientious SMB needs to address security threats as they take action to safeguard their businesses against other threats (loss of customer trust, compliance with applicable laws and regulations, loss of financial solvency) to their businesses.
This complex landscape demands a security strategy that goes beyond just protecting networks. As digital technologies continue to advance, businesses of all sizes, especially small and medium-sized businesses (SMBs), face a constant threat of cyber-attacks.
Xerox understands this vulnerability and offers a comprehensive, personalized approach to workplace security that goes beyond a one-size-fits-all solution. This commitment to risk management stems from Xerox's long history in highly regulated industries. Its secure printing solutions, developed for environments like Navy ships, translate into robust security features for businesses of all sizes.
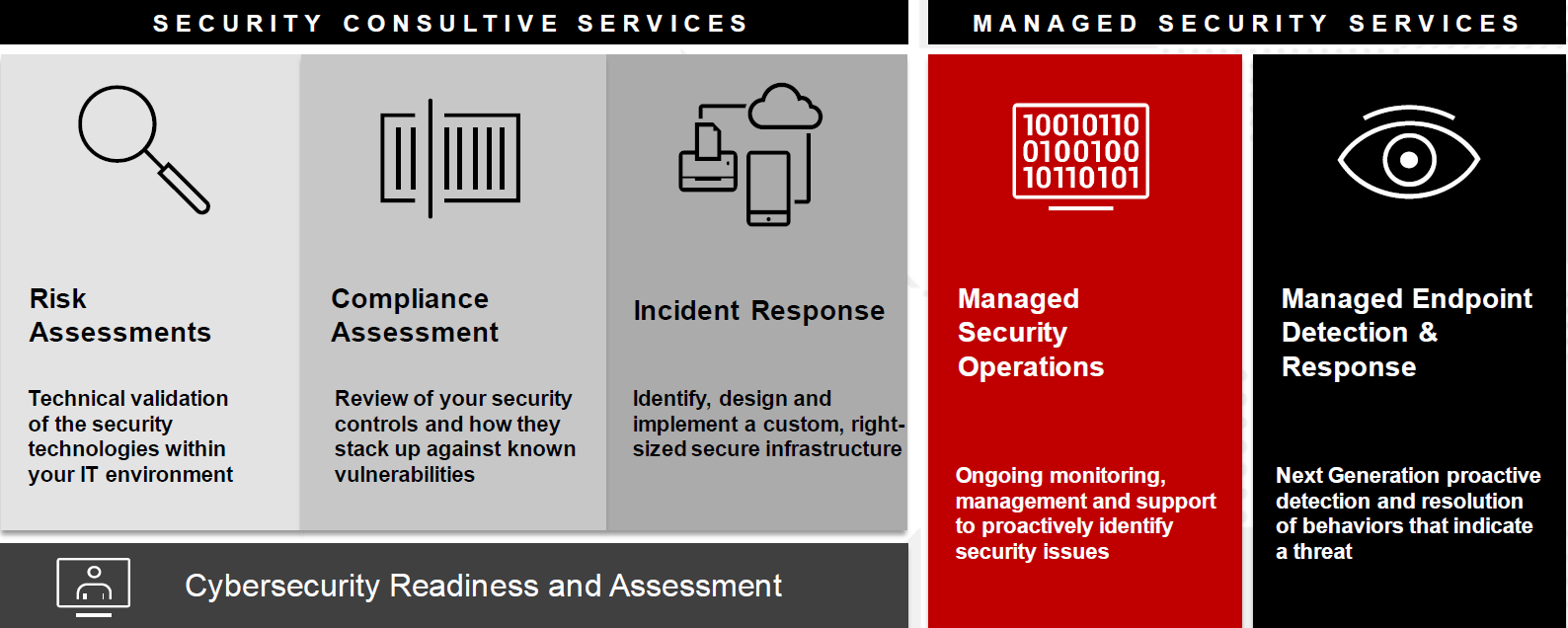
Tailored Security Solutions
Xerox takes a unique approach to cybersecurity, focusing on understanding an SMB's overall risk profile. It believes true security lies in helping SMBs and midmarket firms identify and mitigate these risks, allowing them to innovate without fear of crippling cyberattacks. Unlike a cookie-cutter approach, Xerox recognizes that every business has unique security requirements. Its team of experts works closely with SMBs to assess specific needs and create a personalized package of end-to-end services and solutions. This package includes best-in-class offerings from Xerox's trusted partners, ensuring that SMB clients can access the most advanced technology available.
Techaisle’s SMB and Midmarket Security Adoption Trends research shows high current and planned engagement levels for external firms, such as Xerox, to define and implement security policy, implement security projects, determine overall security strategy, and help choose security technology/products. The survey data shows that selecting the right security technologies is a top issue for SMBs. Security policy is the foundation of cyber success in organizations of all sizes. Suppliers that support the development and roll-out of effective policies play a critical role in helping SMB customers establish effective security postures. Many SMBs and upper midmarket firms lack the depth of experience and “bench strength” needed to manage the implementation of each new security initiative. Suppliers that can offload these tasks help clients to focus experienced staff on the highest-priority management issues. While internal executives often make the “final call” on security strategy, credible third parties definitely have a role in strategy formation.
Xerox’s approach of focusing not just on network security but also on understanding a company's overall risk profile allows it to develop customized solutions that mitigate these risks and empower businesses to thrive in the digital age. Unlike some providers pushing generic solutions, Xerox focuses on understanding clients' business needs. Its technology recommendations are based on how it can best serve clients and improve their operations. This approach ensures that businesses get solutions tailored to their unique challenges.
Xerox offers a two-pronged approach to tackling security challenges: IT Services and Managed Security Services. Its IT Services team is a trusted advisor, helping clients navigate the ever-changing tech landscape and seamlessly integrate these advancements into their digital transformation journey. Meanwhile, Managed Security Services focus on identifying and addressing specific cybersecurity threats. This holistic approach ensures that businesses receive the right technology and the strategic guidance needed to use it effectively. This team works closely with clients to understand their unique vulnerabilities and develop customized solutions. By taking a holistic approach to risk management, Xerox empowers SMB and midmarket firms to thrive in the digital age, free from the constant fear of cyberattacks.
Security for Businesses of All Sizes
While large enterprises often have dedicated security teams, smaller businesses lack the resources to manage complex security needs. Xerox excels at providing tailored solutions for businesses of all sizes. Xerox's large scale allows it to offer a broader range of services and solutions compared to smaller Managed Service Providers (MSPs). It can cater to businesses of all sizes, providing everything from basic network security to complex incident response plans. An example of this flexibility is their "office in a box" solution, which offers pre-configured hardware, networking, security, and compliance features designed explicitly for healthcare franchises. This offering provides HIPAA-compliant hardware, networking, security components, and training – everything a new healthcare franchise location needs to hit the ground running while maintaining compliance. This one-stop-shop approach simplifies security for businesses that may not have the time or expertise to manage multiple vendors.
Xerox's security unit is extensive. It has a dedicated Security Operations Center with a layered approach. Approximately 200 analysts handle “Tier 1 and Tier 2” issues, focusing on resolving low-level threats. More complex incidents are then escalated to Xerox's internal security team and potentially to regional offices for further investigation and resolution. In addition, Xerox leverages its professional services team when necessary.
Xerox Security analysts take the lead in remediation and response. They actively monitor client networks and can stop ransomware encryption attempts in progress. Furthermore, Xerox can develop scripts to neutralize the threat automatically for common malware attacks. Xerox acknowledges the importance of client communication. Its goal is to resolve security issues swiftly and efficiently, minimizing client disruption.
Risk Management in Action
Traditional penetration testing often results in lengthy, technical reports that can be overwhelming for business leaders. Xerox takes a different approach. Its consultative risk assessments involve a collaborative discussion, focusing on the "how" and "why" behind potential vulnerabilities. The goal is to create a straightforward "get well plan" that prioritizes actions and ensures lasting improvements. This focus on actionable risk management goes beyond simply identifying problems; it empowers businesses to address them proactively.
Xerox goes beyond simply selling technology; it focuses on building solid client partnerships. This commitment is evident in their approach to incident response. In the case of a ransomware attack, Xerox's incident response team doesn't just resolve the immediate crisis; it also conducts a forensic analysis to understand how the breach happened. This allows them to develop a "get well plan" with actionable steps to prevent similar incidents in the future. Furthermore, Xerox leverages its partnerships to recommend long-term solutions based on the client's needs, such as migrating to a cloud-based environment for improved security and disaster recovery.
Compliance Made Simple
Navigating the ever-increasing complexity of compliance regulations can significantly challenge businesses. Xerox offers comprehensive compliance assessments that help businesses stay ahead of the curve. This includes Payment Card Industry, FTC Safeguards Rule, and the upcoming Cybersecurity Maturity Model Certification requirement for government contractors. By understanding these evolving regulations, Xerox can help businesses tailor their security strategies to ensure compliance.
Deep Expertise, Delivered
One of Xerox's strengths lies in its extensive network of technology partners. This allows it to offer clients access to highly credentialed experts across various security and networking fields. Imagine needing guidance on the latest endpoint protection solutions for a specific compliance requirement. Xerox can connect the SMB directly with a Cisco expert to discuss Meraki solutions and ensure their specific needs are addressed. This access to a "deep bench" of expertise sets Xerox apart from other security providers that offer more limited solutions. Xerox prioritizes building solid partnerships with its clients. It understands that businesses need solutions that can adapt and grow alongside them. By leveraging its vast partnerships, Xerox developed a scalable security solution allowing a tax franchise to deploy compliant IT infrastructure across multiple locations nationwide quickly.
Xerox recognizes that the cyber threat landscape is constantly changing. It stays up-to-date on the latest threats and adjusts its strategies accordingly. For instance, as ransomware attacks have become less frequent, Xerox has shifted its focus to data exfiltration attempts. It offers solutions to help businesses protect sensitive data and mitigate the risks associated with data breaches.
Unveiling the Engine Behind Making Work Work
Xerox’s approach to cybersecurity prioritizes real-world results over generic solutions. Xerox acknowledges that a one-size-fits-all approach doesn't work in cybersecurity. It tailors its Managed Endpoint Detection and Response (EDR) service to individual client needs. For instance, depending on the client's requirements, it may offer additional security solutions or consultations. Standardized training is crucial for their Managed EDR service. This ensures its security analysts have the expertise required to utilize the chosen platform effectively. Let's delve deeper into how their Managed EDR service functions:
- Going Beyond Benchmarks: Xerox has a dedicated security lab, unlike many MSPs who rely on market trends and vendor ratings. Here, its team thoroughly tests various EDR solutions, including CrowdStrike and Sophos, focusing on specific criteria.
- Prioritizing Real-Time Threat Response: Xerox prioritizes two key factors: speed of response to zero-day threats (unidentified threats) and the ability to prevent endpoint infiltration. It assesses how quickly its remote security operations center can stop a threat and the level of access it has to prevent an infected device from harming a client's network.
- Encryption Protection: Xerox's crucial factor is endpoint protection against ransomware encryption. It specifically looks for solutions with features to prevent such attacks.
- Choosing the Right Tool for the Job: Xerox does not simply pick the most popular EDR solution. Its security analysts evaluate various options based on their effectiveness in a real-world environment, ease of use for the specialists, and the overall ability to mitigate client risks.
- A Multi-Layered Security Approach: Xerox integrates its EDR solution with its Security Information and Event Management system. This allows it to combine network-based threat detection with endpoint data, providing a more comprehensive view of potential security incidents.
- Continuous Improvement: Xerox doesn't settle for a static solution. Every two years, it evaluates new EDR technologies to ensure it has the most effective tools for its clients' needs.
Final Techaisle Take
Most client environments need defenses against many different types of threats, attackers, and threat vectors. Most SMBs lack the internal resources to understand what is required to protect against vulnerabilities and how different “shields” can be connected without leaving (or even creating) exploitable gaps in defense posture. Even the channel members positioned as “trusted advisors” to SMB security clients struggle to keep pace with simultaneous growth in threats and threat actors, vulnerabilities tied to in-use technologies or standard business practices, and the ever-changing security vendor community. Xerox offers a unique and comprehensive approach to cybersecurity. Focusing on risk management, compliance, and deep technical expertise empowers SMBs to navigate the complex world of cyber threats confidently. Its commitment to delivering customized solutions and building solid partnerships ensures businesses of all sizes can thrive in the digital age.
Xerox's consultative approach, extensive partnerships, and focus on business needs position it as a strong player in the cybersecurity landscape. It offers SMBs a combination of scalability, expertise, and service that goes beyond just selling technology. Its commitment to helping clients survive and thrive in today's complex digital world makes it a valuable partner in the fight against cybercrime.
Xerox also prioritizes a Zero-Trust security architecture, which assumes no user or device is inherently trustworthy. This multi-layered approach provides robust protection for devices and data. Security starts at the foundation—Xerox printers are equipped with industry-leading security features and software to prevent unauthorized access and safeguard sensitive information.
Unlike in the enterprise market, where each customer has enough potential economic value to justify extensive direct attention, SMB suppliers need to manage the market programmatically, defining solutions and go-to-market (GTM) strategies that can meet many customer needs without requiring unsupportable levels of direct monetary and human resource investment. In essence, Xerox Security goes beyond simply offering security products. It takes pride in understanding an SMB’s unique needs and challenges. By combining in-depth security expertise with a relentless focus on client service, Xerox is positioning itself as a vital partner in today's ever-evolving cybersecurity landscape.
When you subscribe to the blog, we will send you an e-mail when there are new updates on the site so you wouldn't miss them.












