Techaisle Blog
Connected Security is essential for empowering Future of Work
Security is a feature that needs to be present within each layer of the stack. Security, needs to permeate all layers of an IT solution stack. IT security isn’t a discrete category – it is a ubiquitous factor in all aspects of IT/business infrastructure.
The most important IT-related development in 2018 and beyond will be a focus on connectedness – connected cloud, edge, applications, security, collaboration, workspaces and insights. Internet and the web are the navigation routes that we have been developing since the 1970s; the always-on, everywhere-connected Interwork© platform is the destination that we will be creating in 2018 and for years to come. Please read Future of Work - Interwork: the next step in connected businesses
If there is an evident downside to ubiquitous and constant connectivity, it’s security. In conventional IT environments, security followed a ‘castle keep’-type approach: IT security staff gathered all critical information assets at the core of the environment, and focused their resources on hardening the perimeter, in much the same way that ancient castles used a moat and wall to safeguard people and assets within a central tower.
Today, of course, nations do not use castles as fortifications – and in truth, the traditional approach to security is scarcely better attuned to contemporary IT security needs. With the rise of mobility, cloud and connected supply chains reaching from component suppliers to OEMs to distribution and consumers, there is no perimeter to harden; any sizeable enterprise will have literally thousands of shifting entry points capable of accessing one or more corporate systems. And the rise in the value of information has spawned a sophisticated cyber theft industry: ‘bad actors’ use many different types of tactics and advanced technology to infiltrate corporate IT environments, with an eye towards stealing customer credit card data or internal financial or engineering information, hijacking corporate IT resources or obtaining some other form of benefit.
Security is the most amorphous of IT market categories. Virtually all other technologies occupy a defined position within the solution stack. Today’s security strategies no longer resemble a ‘wrapper’ around assets – they are built into each element of the corporate IT stack and rely on connectedness to (as the NIST framework recommends ) identify threats, protect against attacks, detect intruders if/when they breach perimeter defenses, respond to security events, and recover information lost to theft, loss and/or malware.
For example, in a collaboration or ERP solution, end-point devices access software via a network; the software is in turn housed in a data center or in the cloud; the software reads and writes to/from storage devices; the core application is integrated with other applications that either add to its capability (for example, by providing videoconferencing capability to a collaboration system, or by adding an analytics or reporting to an ERP package); information is backed up to other facilities to provide BC/DR capabilities. In each case, the technologies are assigned to a specific spot within the business workflow or IT stack. Security, though, needs to permeate all layers of the solution: it is used to protect the devices and their connection to the central application, to identify compromise (or malfeasance) of system users, and to safeguard the application itself; to protect the data both as it is in motion and when it is at rest; to build a shield around the data center and the connections between applications; to provide assurance that backups and BC/DR systems don’t become points of exposure for sensitive information. IT security isn’t a discrete category – it is a ubiquitous factor in all aspects of IT/business infrastructure.
It was not always so difficult to position security within the IT firmament. For many years, businesses of all times took an IT security approach that was roughly analogous to the defense strategy in medieval Europe: they built a hardened wall around their most valuable assets, allowed entry only through a carefully-controlled portal (firewalls in IT networks, the drawbridge in castles).
The advent of mobility and cloud, like the introduction of cannons in medieval Europe, made traditional defense strategies obsolete. With mobility and cloud, there is no fixed perimeter to harden and defend – the edge shifts with the physical movement of each device-holding end-user, and the core assets are distributed between owned and as-a-Service facilities. Security is no longer, as is noted above, an attribute that is applied as a wrapper around the IT environment – it is a feature that needs to be present within each layer of the stack, comprised of various tactics and technologies that need to be integrated to ensure that they provide comprehensive coverage, that they do not leave holes between the various shields, and that they are able to respond to new threat sources as they arise. Security is built into each element of the corporate IT stack, and rely on connectedness to identify threats, protect against attacks, detect intruders if/when they breach perimeter defenses, respond to security events, and recover information lost to theft, loss and/or malware.
At a technical level, cybersecurity professionals use their own version of “connected security” – with the cyber (or intrusion) kill chain, they link the different stages in a cyberattack, aligning appropriate responses and technologies with each stage.
Figure below provides an intriguing view of the connections that shape contemporary security techniques. The seven graphics at the top show a chain of logic that describes an attacker’s sequence: reconnaissance (investigating and testing targets), weaponization (adding malware to legitimate files), delivery (transmitting the malware via attachments, USBs, etc.), exploitation (gaining control of some part of a target’s environment), installation (creation of an access route that can be used by attackers), command and control (establishing control over the remote system/application) and actions on objectives (theft of data, etc.). The bottom set of six graphics describes defender actions that are used to combat the intruder at each stage of the attack. Beneath the detect, deny, disrupt, degrade, deceive and destroy defense sequence, higher level objectives describe key steps in processes that use shared intelligence to combat APTs (advanced persistent threats). Ultimately, the knowledge gained through this approach is collected in what one white paper described as a “community attack model…a process to gather lots of relevant real-life information about successful attacks and organize it in a way that helps enterprises make good choices about the most effective defensive actions they can take".
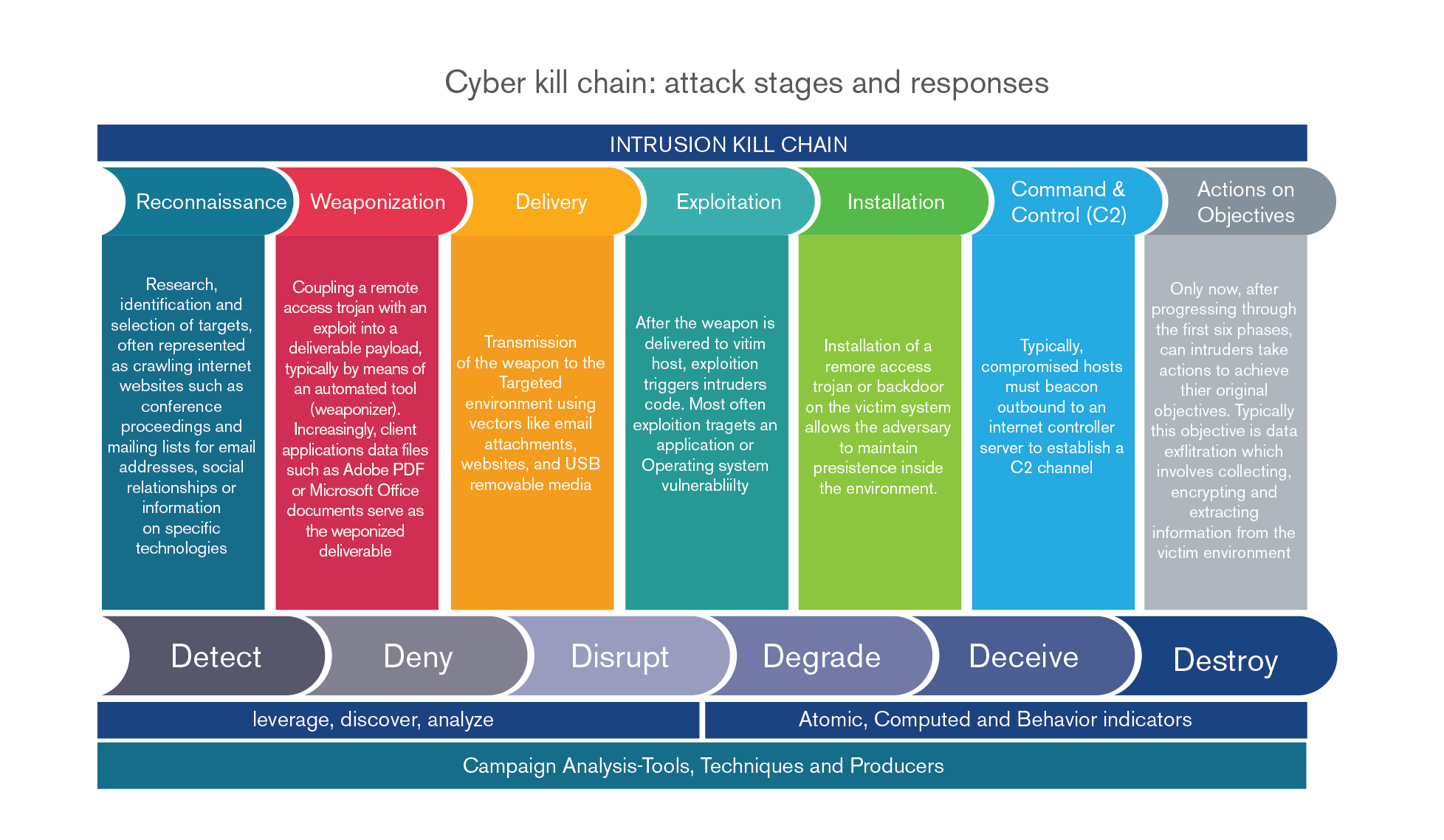
Source: “Framework for Improving Critical Infrastructure Cybersecurity.” National Institute of Standards and Technology, February 12, 2014
In today’s world, “connected” is an essential component of “security.” Organizations need to deploy security strategies that are aligned with the needs of infrastructure combining multiple connected platforms, applications and users; they need to respond to connected stages in attacks with similarly-coordinated defensive tactics; and they need to capitalize on the ability to pool data to increase defender awareness of attack methods and counteractions. Connected security is an essential property future of work - the Interwork© platform.
When you subscribe to the blog, we will send you an e-mail when there are new updates on the site so you wouldn't miss them.