Techaisle’s global SMB survey shows that mobility security is the 2nd top IT challenge for small businesses and 4th top IT challenge for midmarket businesses. To delve deeper, during the course of the Techaisle SMB 2015 Mobility Adoption & Trends survey, respondents were asked “When it comes to security risk in the mobile computing context, which of the following represents a source of exposure or uncertainty within your organization?” To a surprisingly high degree of candidness SMB concerns with mobility security revolved around users. As figure below demonstrates, SMB IT respondents ranked three user-attributable issues
- User neglect/irresponsibility,
- Lack of user knowledge/awareness, and
- User mishap
amongst their top five concerns, trailing only “general malware infection” as a mobility security threat. Data is where the user is and to say that the enemy is inside the tent would be an understatement.
SMBs recognize the exposure and vulnerability but Techaisle survey shows that only 16% of SMBs worldwide are fully prepared to handle mobility security challenges. Data also shows that like manageability, security is an important constraint on mobility adoption within the SMB market. Most MSPs, channel partners and suppliers continue to focus on BDR and/or anti-malware security as they are easy to offer and deploy but they represent a very narrow approach to larger security issues within SMBs.
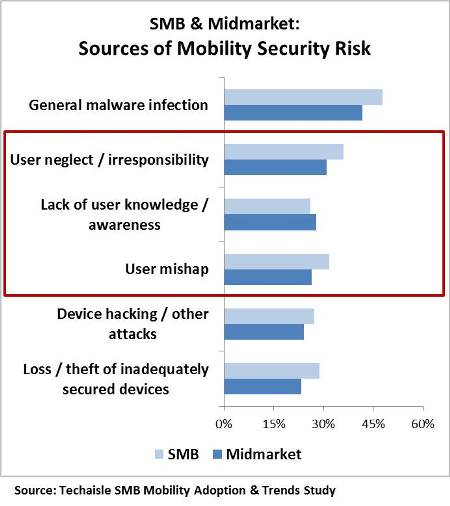
Although there are differences between small and midmarket perceptions but across all SMBs the angst about user neglects, irresponsibility, mishap is real and Techaisle believes that it reflects a concern about the effect that mobility has on the IT security perimeter.
Security Perimeter: Medieval castle design vs. windows and breezeways
The traditional approach to IT security has resembled the security approach reflected in medieval castle design. In castles, noblemen built high, strong walls around precious assets (themselves, as well, important citizens) and gathered peasants and cattle inside when threats loomed. IT has traditionally taken an analogous approach: harden the network perimeter (the firewall) and deal with threats, such as malware, if and when they arise.
The problem with mobility (like cloud) is that it changes the concept of “perimeter.” Intruders do not need to batter through closely-guarded walls to gain access to the interior of the network; they can ride through a permeable configuration on the backs of mobile devices that have been granted access to the precious applications and data that live in the interior of the organization.
Castle walls and drawbridges have been replaced by windows and breezeways offering access to visitors arriving from all directions.
With mobility, the user community becomes a ubiquitous and shifting source of portals through the perimeter. As a result, IT doesn’t need to only defend against recognized foes: it needs to protect the corporation from breaches that can result from the actions of its own workers, and needs to protect the same data that it delivers as an essential component of support for the mobile workforce – the workforce that is viewed by senior management as making compelling contributions to the top and bottom-line success of the business.
IBM is increasingly coming across the above scenario within its current and potential midmarket customer base. Speaking with Techaisle, IBM’s Director of Global Mid Market and MSPs, Brig Serman said “we are finding an increasing issue around balancing the security of company assets with the privacy concerns of the employee when using their BYOD device. IBM’s approach has been to address the security requirements of the business specific applications and data, while leaving "personal" data untouched. This goes a long way in addressing this balance, especially in an environment where increased mobility and the blurring of work / personal use of these devices becomes the norm”.
Layered framework strategy
In many ways, it is difficult or impossible to isolate security as an issue in mobility. Security is intrinsic to the devices, applications and solutions used by SMB firms that have adopted mobility, and security is an essential factor in supporting the mobile workforce. Looking at the list of threat sources detailed by SMB respondents in above figure, it is clear that IT needs to move beyond the perimeter as a means of defining security and to safeguard precious data and application assets through a combination of:
- monitoring,
- network segmentation,
- encryption and related tactics
This clarity, though, does not by itself help SMB IT staff to adjust to the new threat sources that accompany mobility solutions. Suppliers will need to work with SMB and midmarket clients to create layered strategies that can evolve with the expanding mobile workforce, its activities and its requirements.
With 42% of global SMB employees becoming mobile in 2015, IT Suppliers (vendors and channel partners) need to help their SMB clients establish frameworks that protect against both external and employee threats to information security.